Website Security in 1C-Bitrix. Tools against Hacking
Proactive protection against website hacking
The proactive filter is an important tool in the fight against website hacking. It detects and blocks most known attacks and protects against security flaws that may be made by developers. However, like any other protection, it is not 100% effective and may sometimes give false positives. Therefore, in addition to the proactive filter, other measures must be taken to protect the site, such as using complex passwords, regularly updating and checking the system for vulnerabilities.
The website security scanner is a tool that helps assess the level of website security, detect potential vulnerabilities in software, and identify incorrect security settings for CMS, PHP, and the server. This service is designed to help website owners protect their resources from hacker attacks and other malicious actions. After scanning the site, the security scanner issues a report on the problems found and recommendations for their resolution. This allows vulnerabilities to be promptly eliminated and the level of site security to be increased.
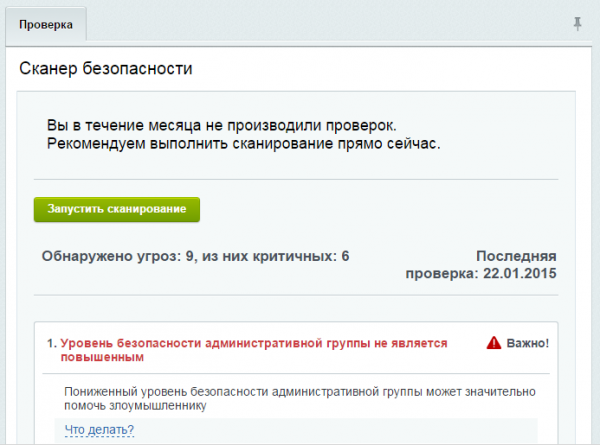
To start scanning a website, simply click on a button. Upon completion of the scan, the scanner will display the results with a full list of all security threats detected on the site.
The internal organization of the site will be checked for deficiencies such as whether sessions are stored securely or not. The module will also show which security system features are not being used, and which settings are not configured. Additionally, the scanner will detect all non-dangerous but potentially vulnerable areas of security, such as a simple password for the database or a lowered security level for administrators, etc. These minor details can be useful if the developer forgot to adjust something after completing their work.
Web antivirus. Protects the site from viruses
The web antivirus is a tool that protects a website from viruses. This is the easiest way to protect a website from virus infections. Usually, the infection of a website with viruses occurs from the administrator's computer, which has access to the website, rather than from the fact that the website is online for an extended period of time.
The main task of the web antivirus is to notify the website administrator about a possible infection. If the website is infected with a virus, it may mean that the virus is also present on the administrator's computer, and appropriate measures are necessary.
Web antivirus works on the website rather than on the administrator's computer, so to ensure complete protection, it's also necessary to use regular antivirus software on the administrator's computer. Depending on the settings, the web antivirus may only inform the site administrator about suspected virus infection or automatically detect malicious sections in the website's HTML code and remove suspicious iframes and JavaScript. Additionally, exceptions can be added to prevent the web antivirus from triggering on safe but suspicious code sections. Web antivirus plays an important role in blocking the spread of viruses through your website, ensuring its security, and protecting against potential threats.
Control of Suspicious Activity on the Website
Control of suspicious activity on the website can be achieved through various tools and technologies. One of the most common methods is using specialized scripts and programs that can analyze user activity on the site and block those who exhibit suspicious behavior. For example, an IP address blocking system can automatically block access to the site for users with certain IP addresses that make too many requests to the site or exhibit other suspicious activity.
In addition, to control suspicious activity on the website, special services such as Google reCAPTCHA can be used, which allows distinguishing bots from real users. Another method of control is the analysis of server logs, which record all requests to the site. Such analysis can detect suspicious activity and take measures to block it. Finally, there are special website security monitoring systems that automatically analyze activity on the site and can prevent many types of attacks, including DDoS attacks and password guessing attempts.
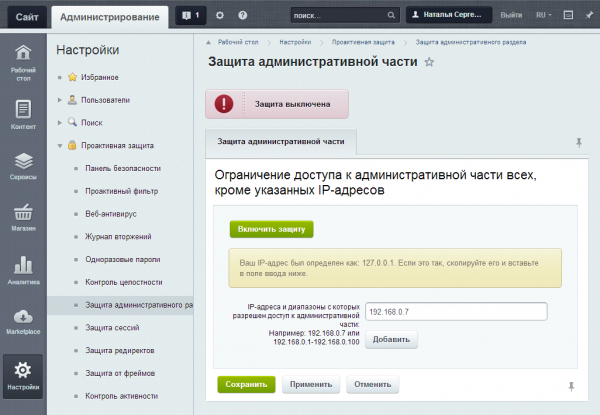
Protection of the Administrative Part
Protecting the administrative part by IP address is an effective way to prevent unauthorized access. To do this, access rules to the administrative part of the website must be configured in such a way that access is only allowed from specific IP addresses.
However, it should be noted that this method is not absolutely reliable. For example, a malicious actor can use VPN or proxy servers to hide their real IP address and gain access to the administrative part of the website.
In addition, using IP address protection may lead to difficulties if the website administrator works from different locations or uses different devices to access the administrative part.
Therefore, it is recommended to use multiple methods of protection in combination, such as password protection and two-factor authentication, to ensure maximum security of the administrative part of the website. Additionally, it is important to keep software up to date and eliminate vulnerabilities that could be exploited by malicious actors to gain access to the administrative part of the website.
Session protection
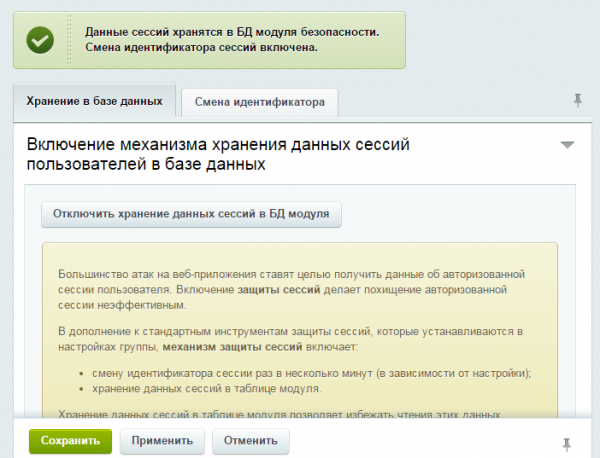
Session protection is an important security measure for web applications. It prevents session theft and, consequently, a malicious actor gaining access to a user's authorized account. A session is a temporary mechanism used to track a user's activity on a website during a browsing session. When a user logs in to a website, the system creates a unique session that links them to a specific account. The session identifier is usually passed through a cookie or GET parameter in the URL.
A malicious actor may attempt to intercept this identifier and use it to gain access to a user's account. To prevent this, session protection usually includes the use of cryptographic encryption and hashing methods, as well as unique session identifiers.
In 1C-Bitrix, there is a possibility to use session protection, which includes storing session identifiers in the database and setting session lifetime. This allows the system to automatically change the session identifier at specified time intervals, making session hijacking meaningless. It is also important to ensure that the application does not transmit confidential information through GET parameters in the URL, as this can lead to data leakage through the browser history or server logs.
Two-Factor Authentication and One-Time Passwords
To improve the security of website login and protect against password leakage, there is a mechanism for two-factor authentication. It involves entering two different pieces of data to confirm the user's identity. In addition to the password, the user must enter a one-time code, which can be sent to their mobile phone or email. One-time passwords can be generated programmatically or sent to the user's device as an SMS or message in a mobile application. They are valid only once and cannot be reused. Thus, even if a malicious actor steals the password, they cannot gain access to the account without the one-time code. Two-factor authentication and one-time passwords significantly increase the security of website login and protect against hacking, especially in case of password leakage. These mechanisms can be easily implemented on most popular platforms and frameworks, including 1C-Bitrix.
Website Protection Against DDoS
Protecting a website from DDoS attacks is an important task for any website, especially if it is a large project. A proactive filter can help combat DoS attacks and protect the site from simple DDoS attack methods. However, for more serious attacks, such as Distributed Denial of Service (DDoS), more powerful protection is required. Contact our company to choose an effective service for protection against DDoS attacks.







